Cyber Criminals Phishing for Account Access
Por um escritor misterioso
Descrição

True Stories: Use 2-Factor Authentication for Extra Login Safety

Phishing: Best practices for cybercrime prevention - GoTo

Anatomy of a Phishing Attempt – THE SAFE

Phishing by hackers and cybercriminals, identity theft, password
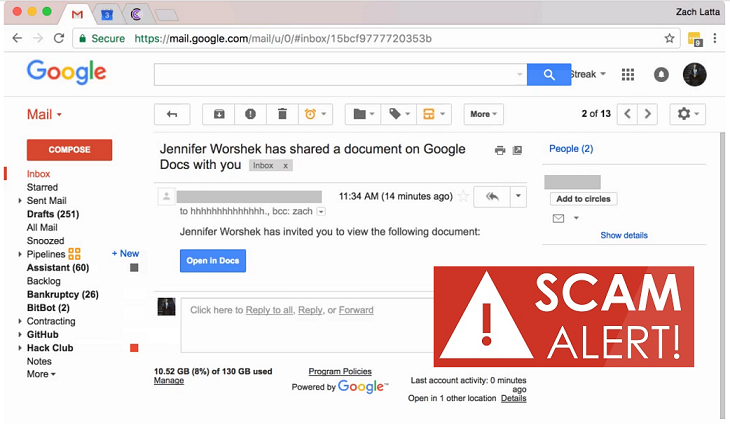
Blog NASA Federal Credit Union

How Cybercriminals Use Social Engineering to Access Sensitive

Cyber Security Awareness Month

Reducing Personal Cybersecurity Risk > U.S. Navy - All Hands

When It Comes to Fraud, Where Is the Weakest Link?
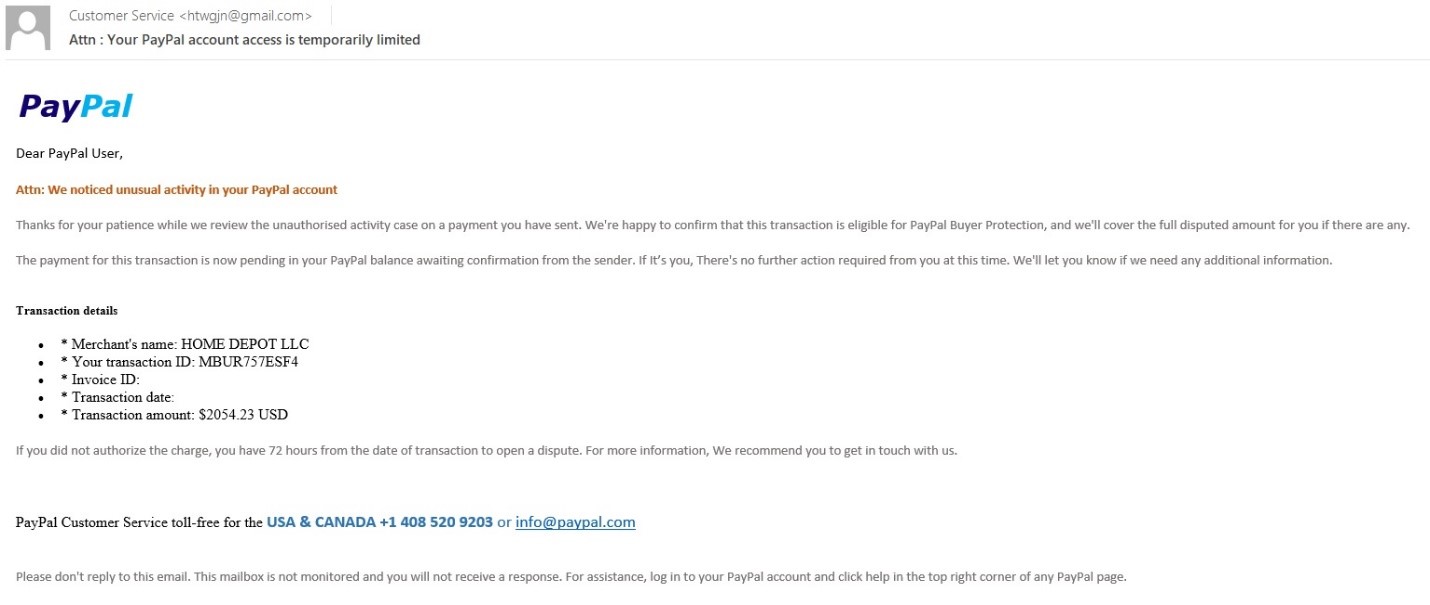
Cybercriminals are actively using vishing at a growing rate
Internet phishing, hacking, computer security fraud and cyber
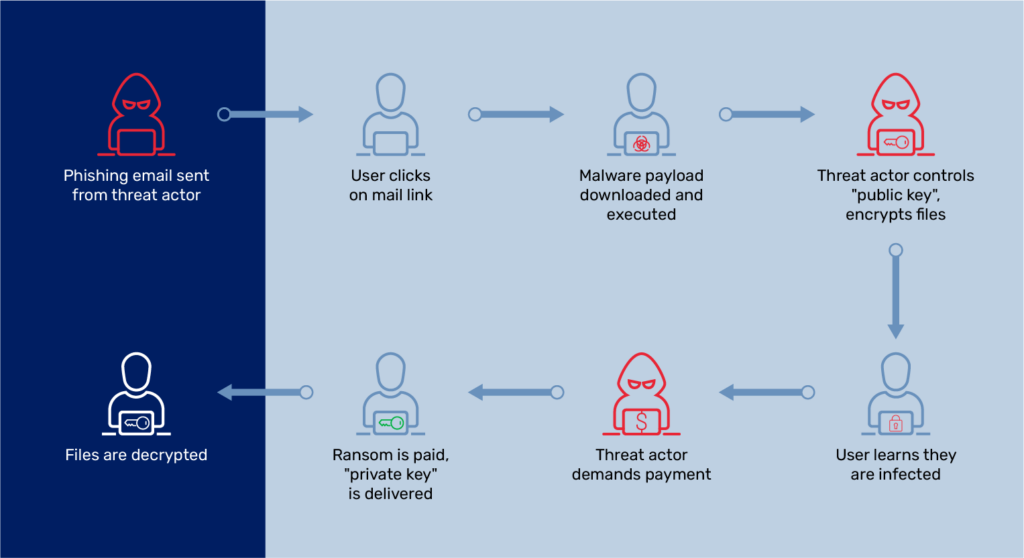
Cyber Criminals

Do Online Access Imperatives Violate Duty of Care?

Cybercriminals Deliver Async Remote Access Trojan in New Resume
de
por adulto (o preço varia de acordo com o tamanho do grupo)




/i.s3.glbimg.com/v1/AUTH_59edd422c0c84a879bd37670ae4f538a/internal_photos/bs/2018/1/A/AmPxQFQCa8UwBTyrcwEg/prefeitura-princesa-isabel-pb.jpg)