Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Descrição
Describing activities of a crime group attacking Ukraine.

So long and thanks for all the 0day, NCC Group Research Blog
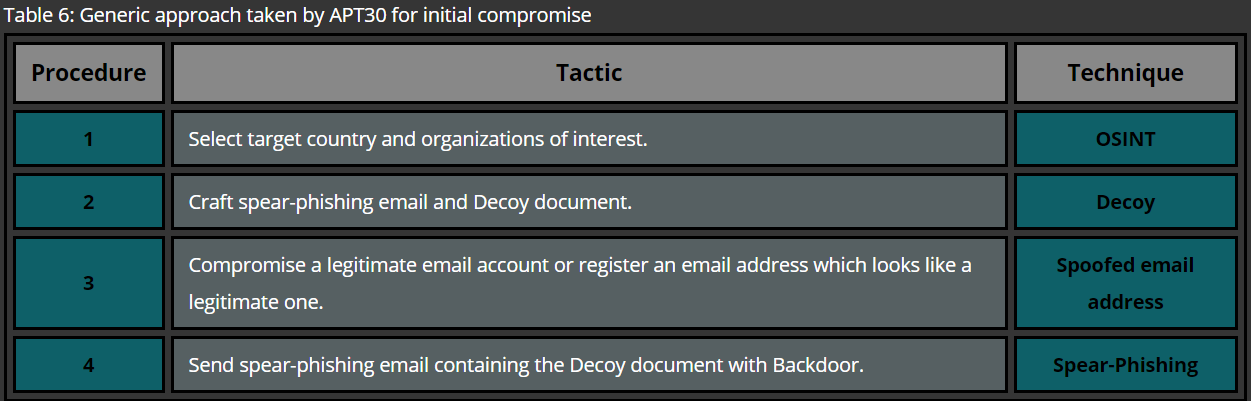
Initial Compromise

Vault 7 - Wikipedia

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

PDF) Money Over Morals: A Business Analysis of Conti Ransomware

Initial Access Brokers - who are they, what do they do, and how can you protect yourself?

Blogs Dell Technologies Info Hub

Initial access brokers: How are IABs related to the rise in ransomware attacks?
Information March 2023 - Browse Articles
de
por adulto (o preço varia de acordo com o tamanho do grupo)







