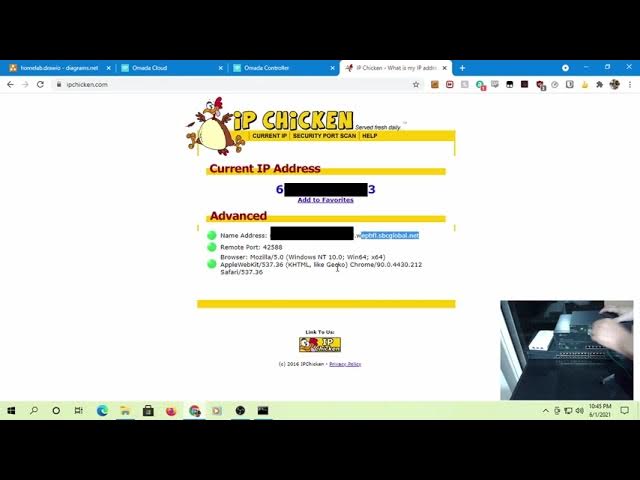
Malware analysis Suspicious activity
Por um escritor misterioso
Descrição
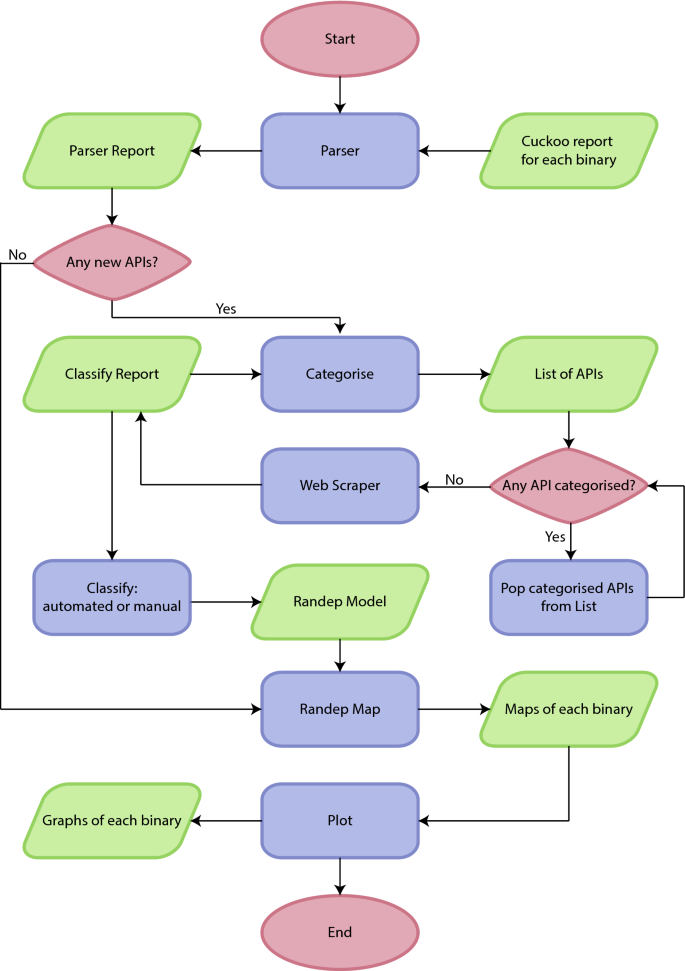
Ransomware deployment methods and analysis: views from a
What is Malware Analysis? - SOC Prime

Top 10 Malware Analysis Platforms & Tools

How to Detect New Threats via Suspicious Activities

Behavioral blocking and containment: Transforming optics into

Fileless malware threats: Recent advances, analysis approach

How Malware Analysis Works - NetWitness Community - 669511

1. General Flow of Signature-Based Malware Detection and Analysis
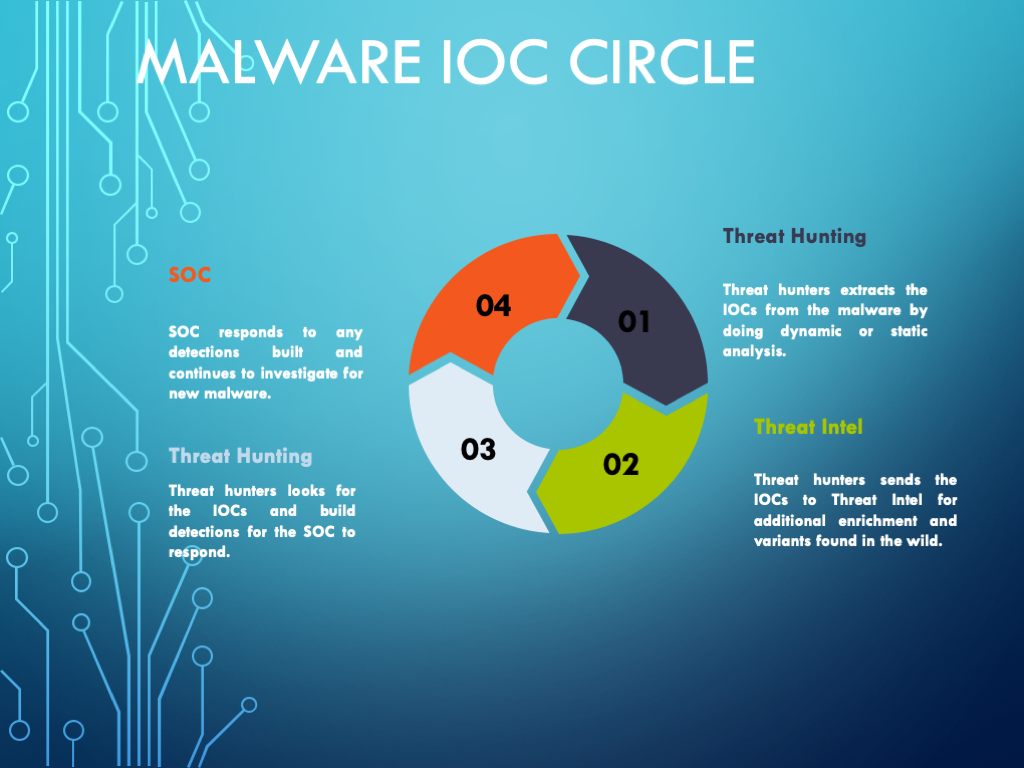
Malware Analysis Framework v1.0
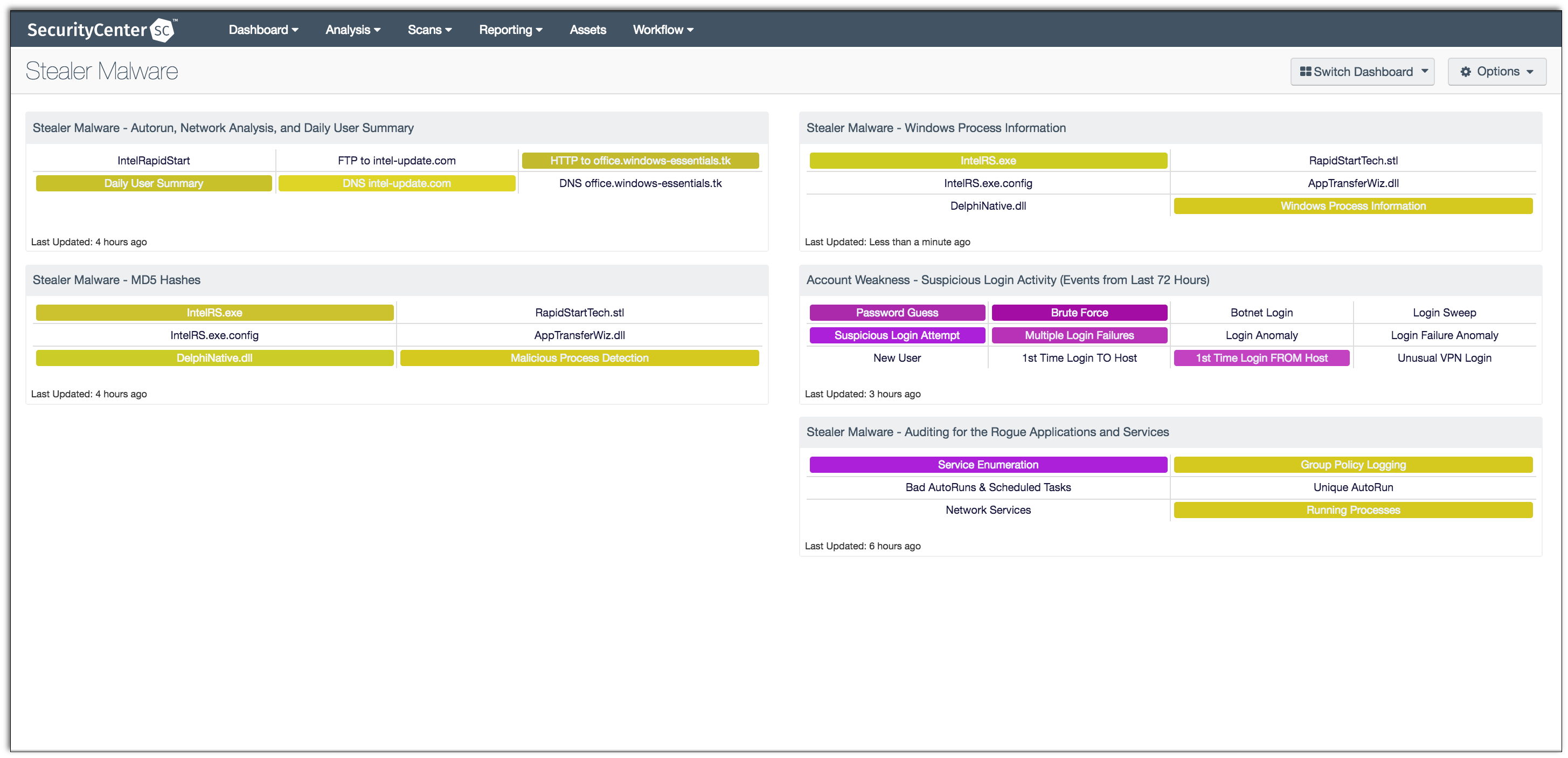
Stealer Malware - SC Dashboard

Windows Servers Security: How to Look for Suspicious Activities

Microsoft 365 Alerting - Detect and React to Threats Instantly

Top 10 Malware Analysis Platforms & Tools
de
por adulto (o preço varia de acordo com o tamanho do grupo)