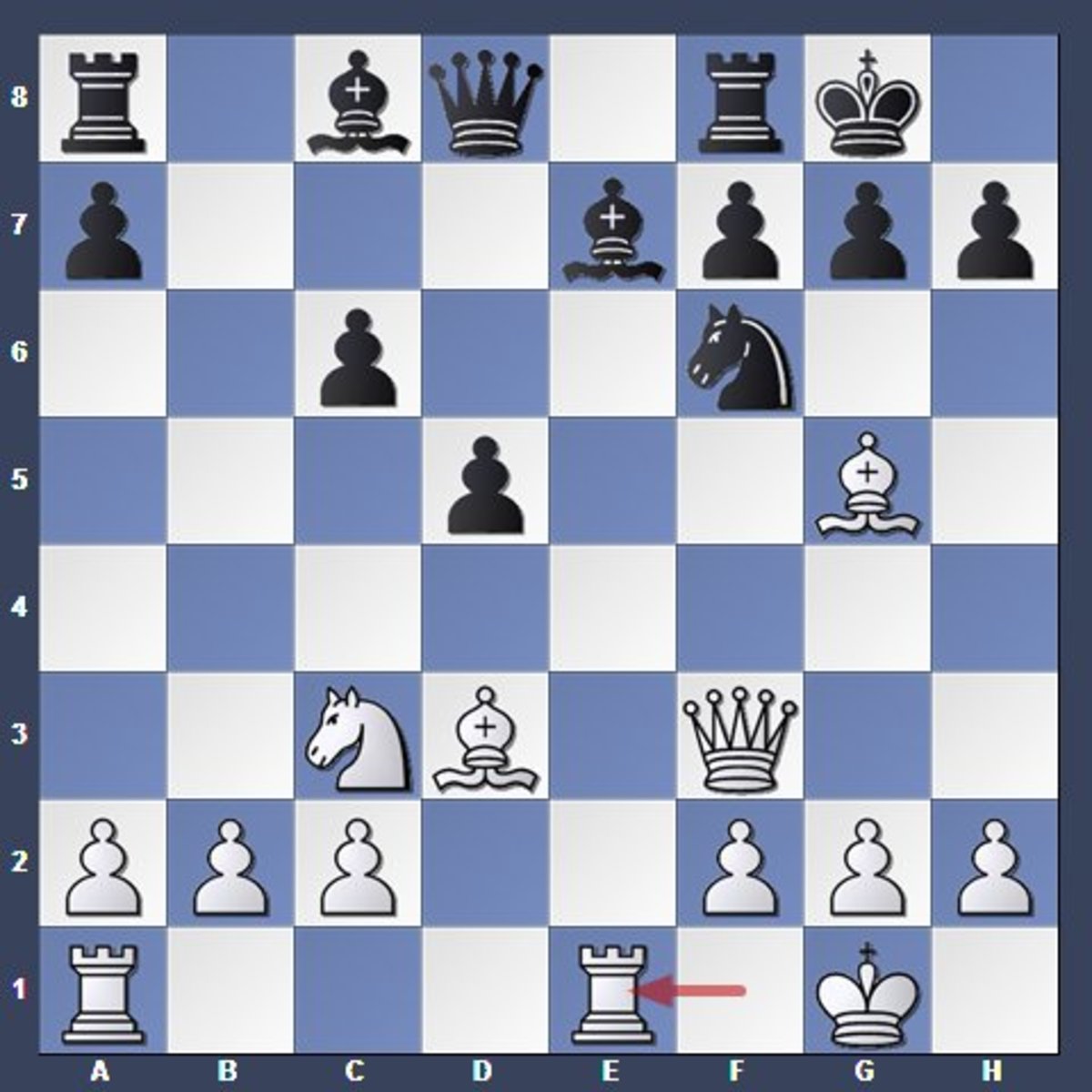
Open Files: How Do You Exploit them?
Por um escritor misterioso
Descrição
It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…
Kernel Exploits Part 2 – Windows Privilege Escalation

Windows Takeover with a PDF File

Exploit PDF Files, Without Vulnerability - 404 Tech Support

How to Exploit WebDAV on a Server & Get a Shell « Null Byte :: WonderHowTo

Basic Exploitation with Metasploit: Windows: HTTP File Server

Very simple exploit shown to completely bypass Gatekeeper security software in OS X - Neowin
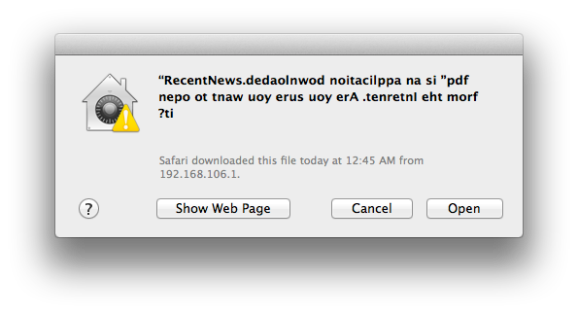
Mac Malware Uses Right To Left Character Exploit
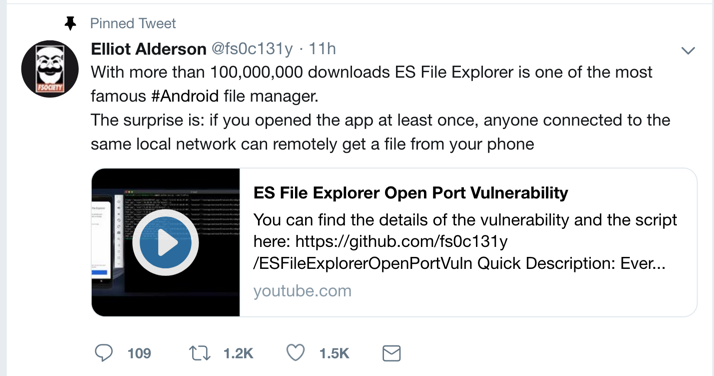
Proj 9: ES Explorer Command Injection (10 pts)
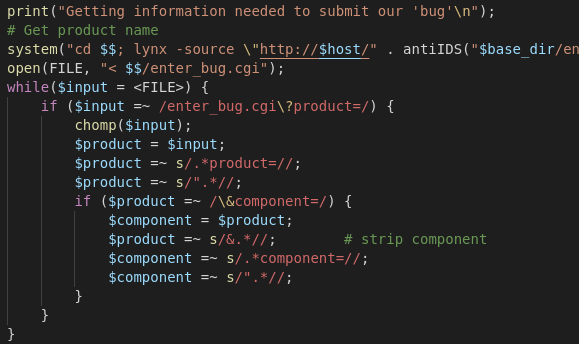
Exploit Wars II - The server strikes back
de
por adulto (o preço varia de acordo com o tamanho do grupo)