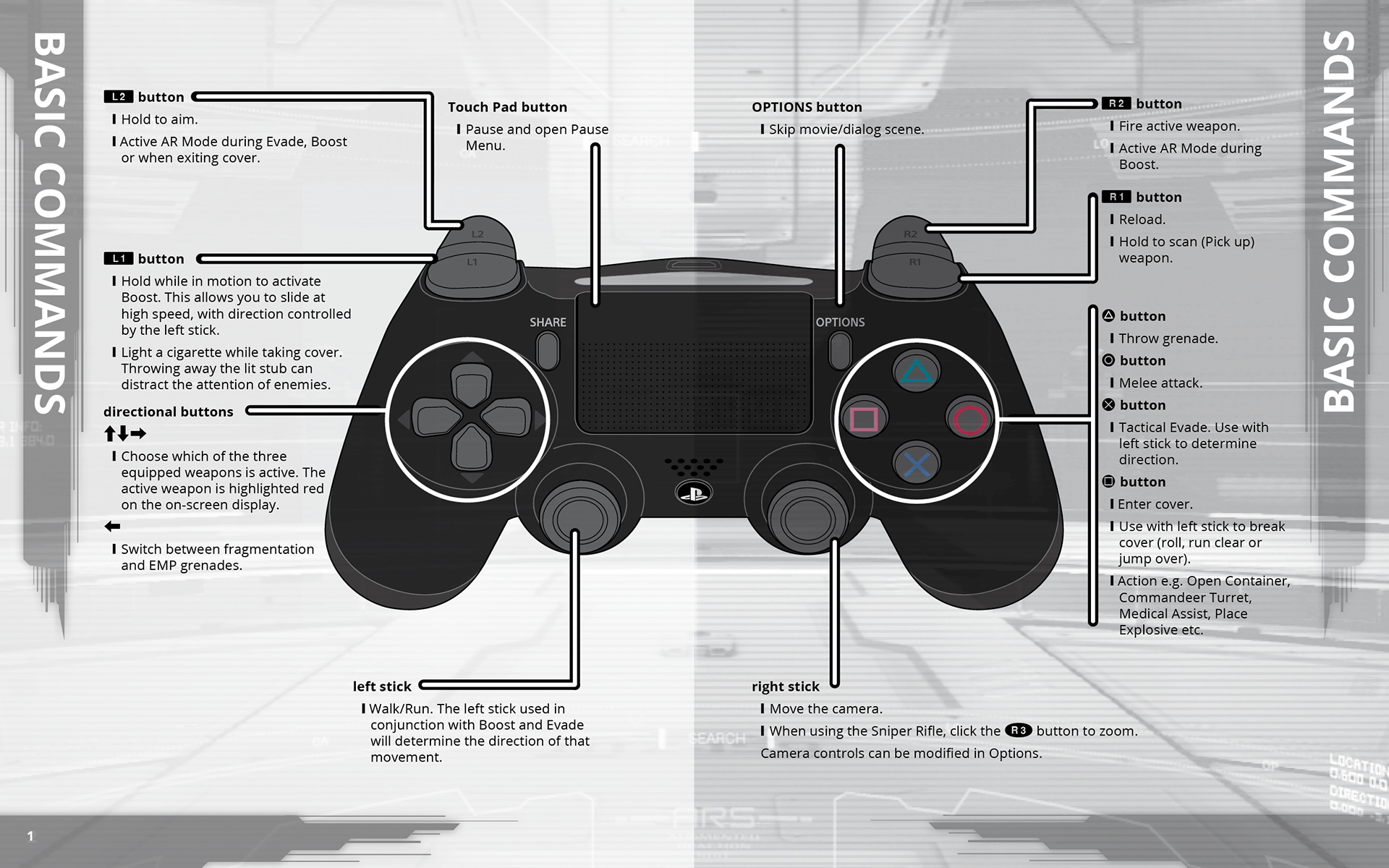
Suspicious User Controls
Por um escritor misterioso
Descrição

What Is Email Security? Definition, Benefits, Examples & Best Practices - Spiceworks

Stronger Access Control Management - Enterprise Network Security Blog from IS Decisions
Understanding HP Wolf Identity/Credential Protection
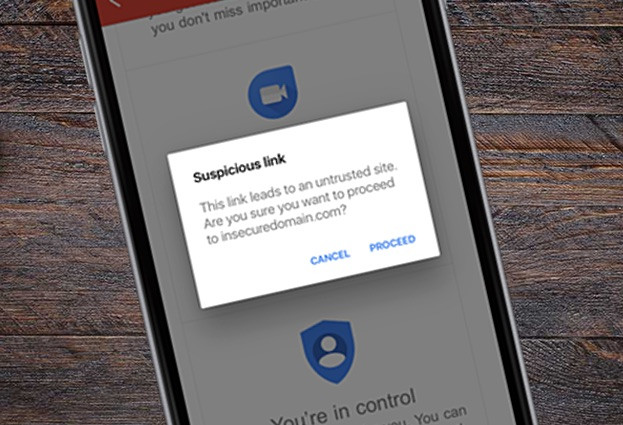
Links in Gmail now warns iOS users about suspicious links, in fight against phishing threats
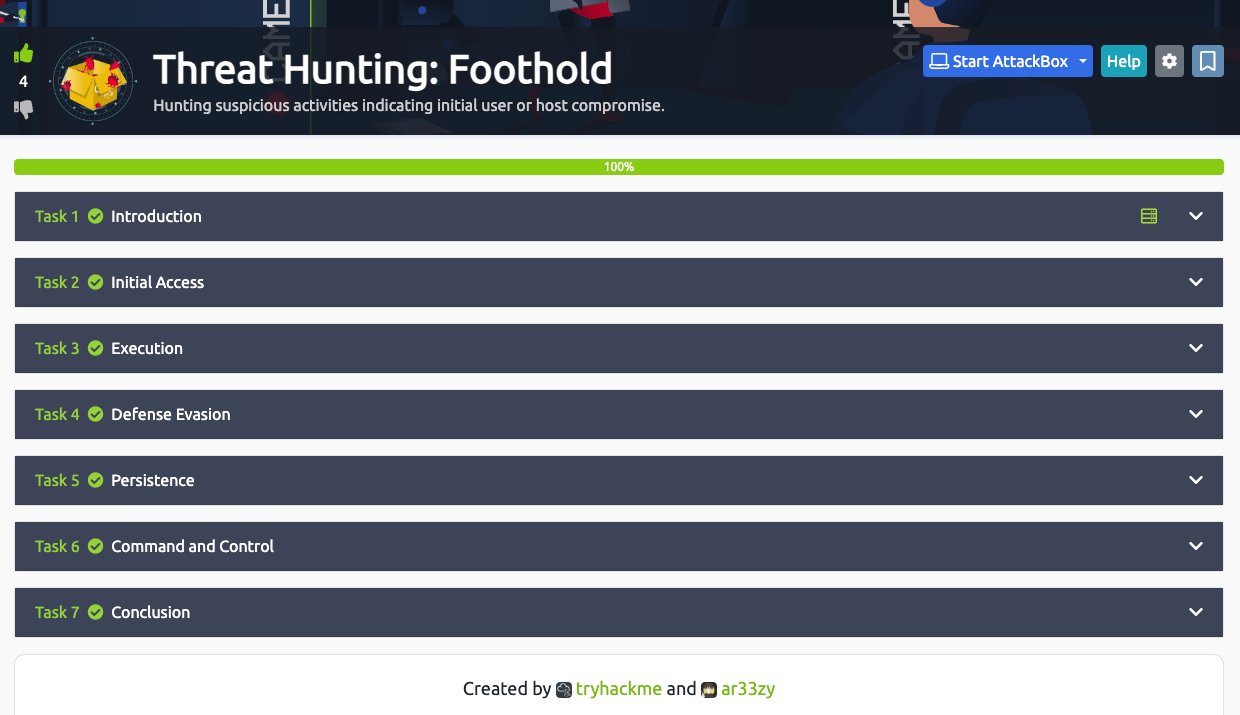
TryHackMe on X: NEW ROOM: Threat Hunting: Foothold It's time to hunt for suspicious activities indicating initial user or host compromise! 🧠 Build an attacker mindset with MITRE tactics 🙌 Apply threat

Chapter 7 Activity: Testing and Monitoring Security

Control input on suspicious sites with Cloudflare Browser Isolation

PCI DSS Compliance Solution Brief

How to fix this Suspicious activity was detected from your network (PK), cannot complete sign up. : r/ControlD
de
por adulto (o preço varia de acordo com o tamanho do grupo)