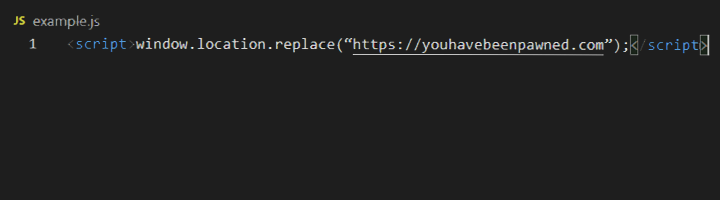
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Descrição
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…
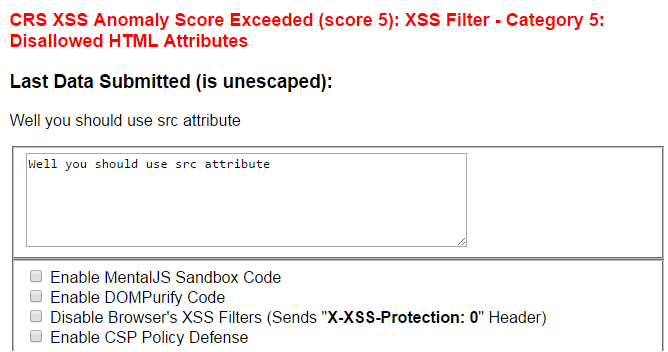
Sucuri WAF XSS Filter Bypass - Miscellaneous Ramblings of a Cyber Security Researcher
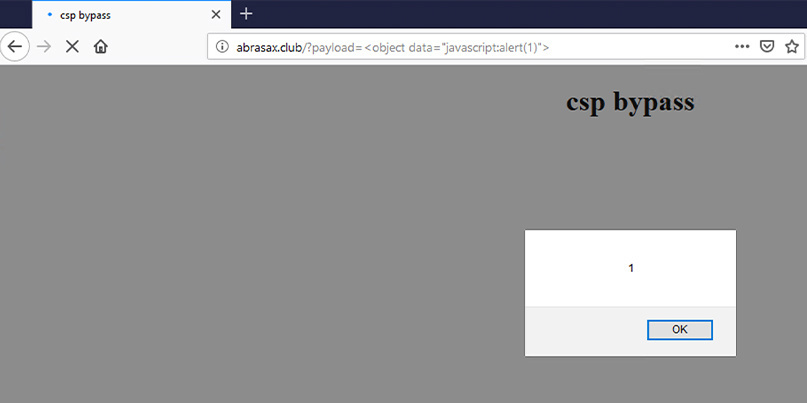
Firefox vulnerable to trivial CSP bypass

XSS Filter Evasion
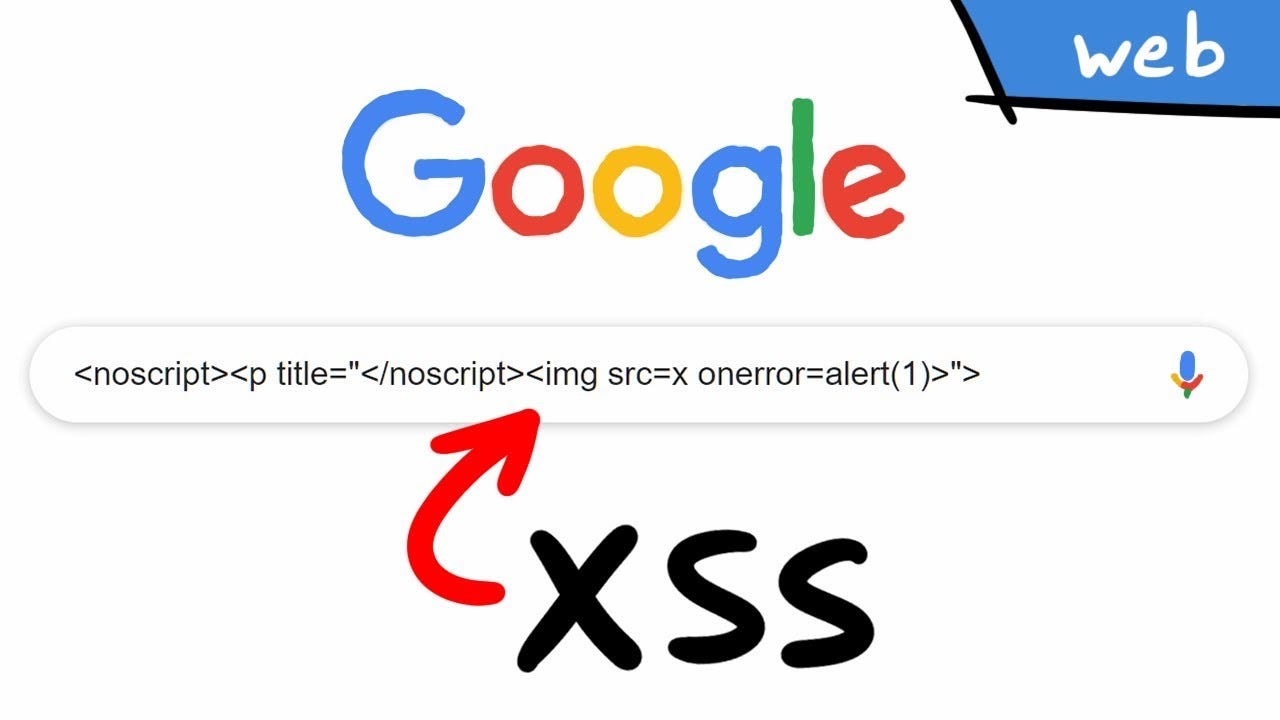
Cross Site Scripting ( XSS ) Vulnerability Payload List, by Ismail Tasdelen
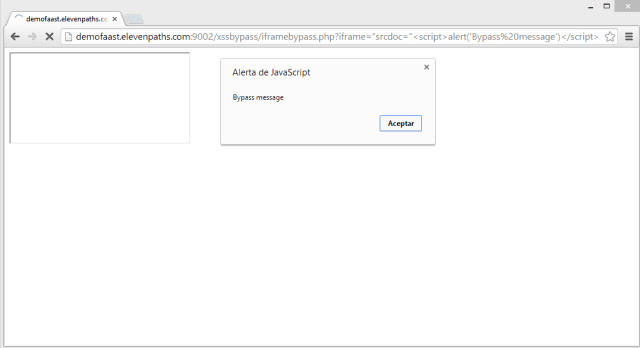
How to bypass antiXSS filter in Chrome and Safari (discovered by ElevenPaths) - Think Big
What are some ways of protecting against cross-site scripting (XSS) injection through cookies? - Quora
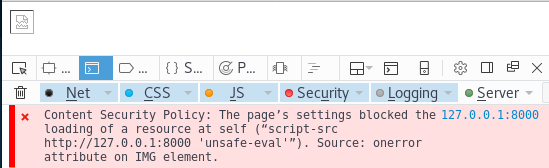
Bypassing modern XSS mitigations with code-reuse attacks - Truesec

LDAPFragger: Bypassing network restrictions using LDAP attributes, NCC Group Research Blog

ZTWeb: Cross site scripting detection based on zero trust - ScienceDirect

Node.js Security: Preventing XSS Attacks
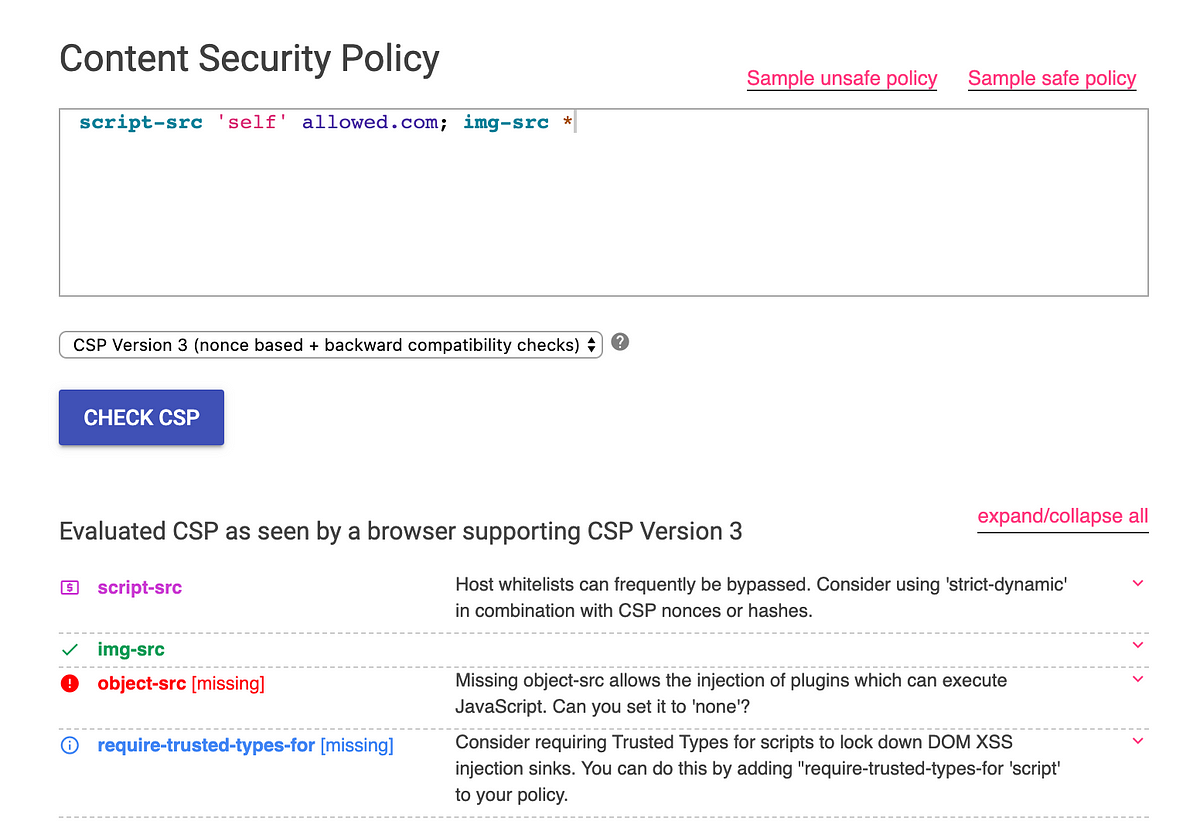
Content Security Bypass Techniques to perform XSS
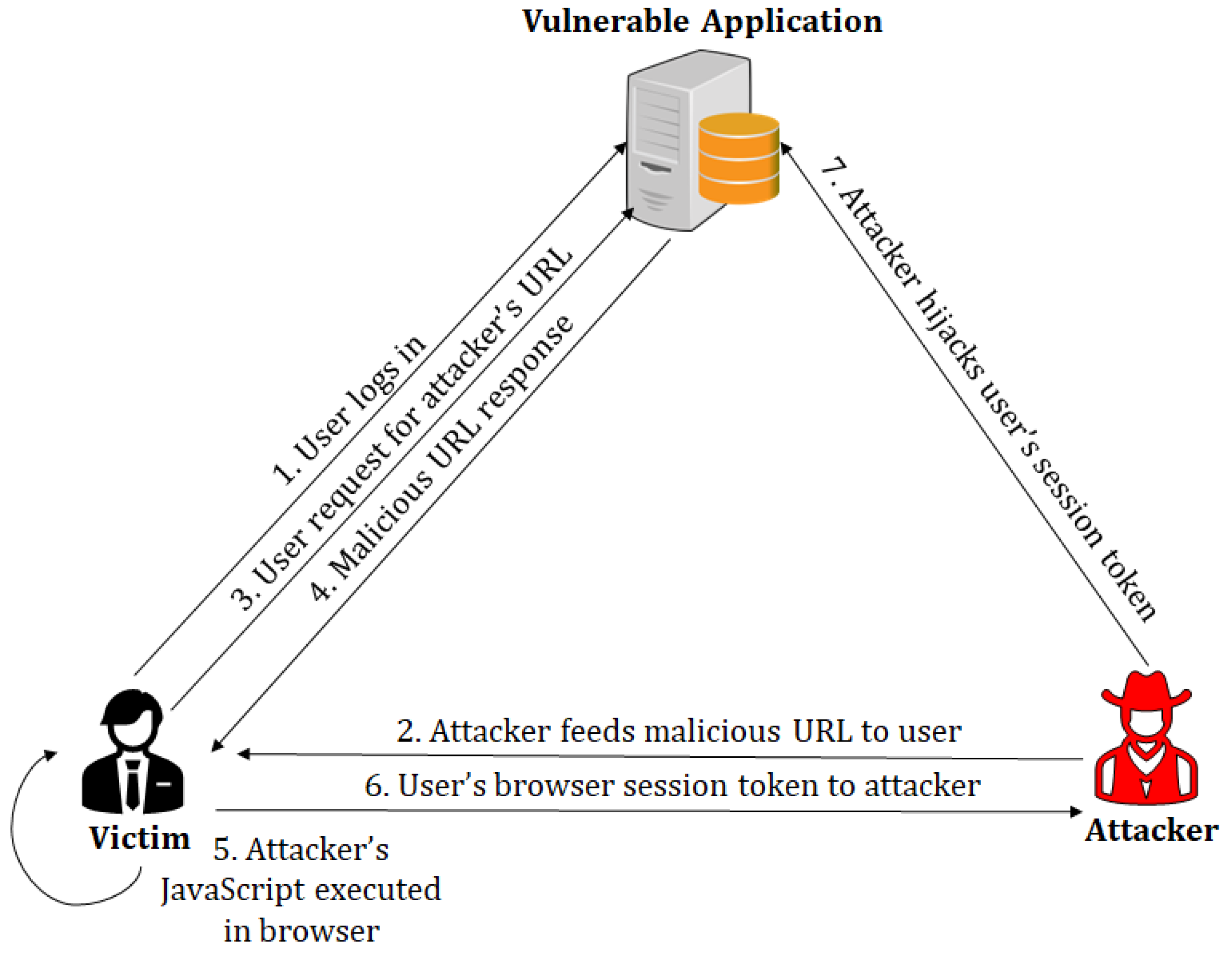
Sensors, Free Full-Text
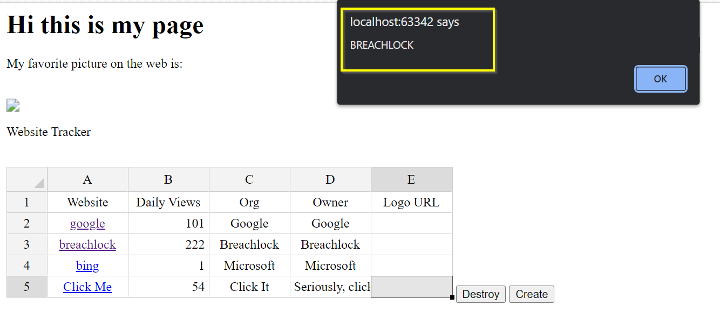
How to Fix XSS Vulnerabilities on Web App Links - BreachLock
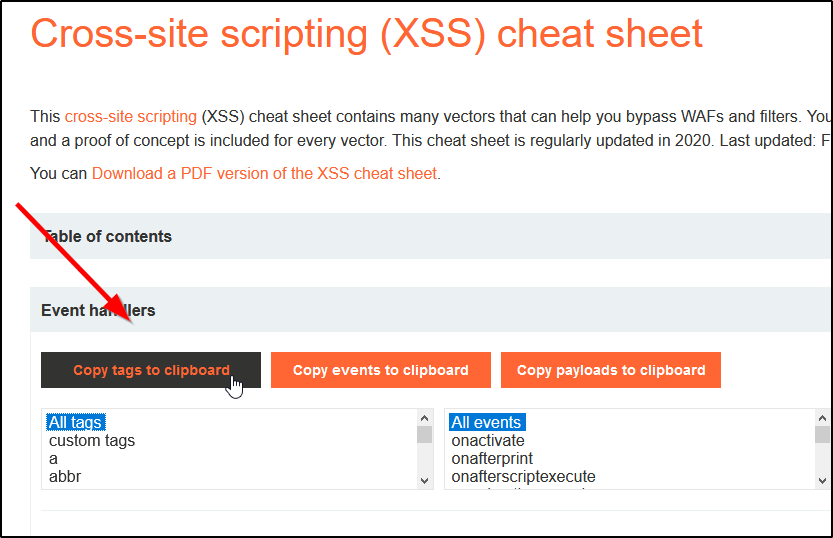
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
de
por adulto (o preço varia de acordo com o tamanho do grupo)