Cybercriminals are circumventing email security with image-based
Por um escritor misterioso
Descrição
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't

VIPRE finds 233.9 million malicious emails detected in Q3 2023
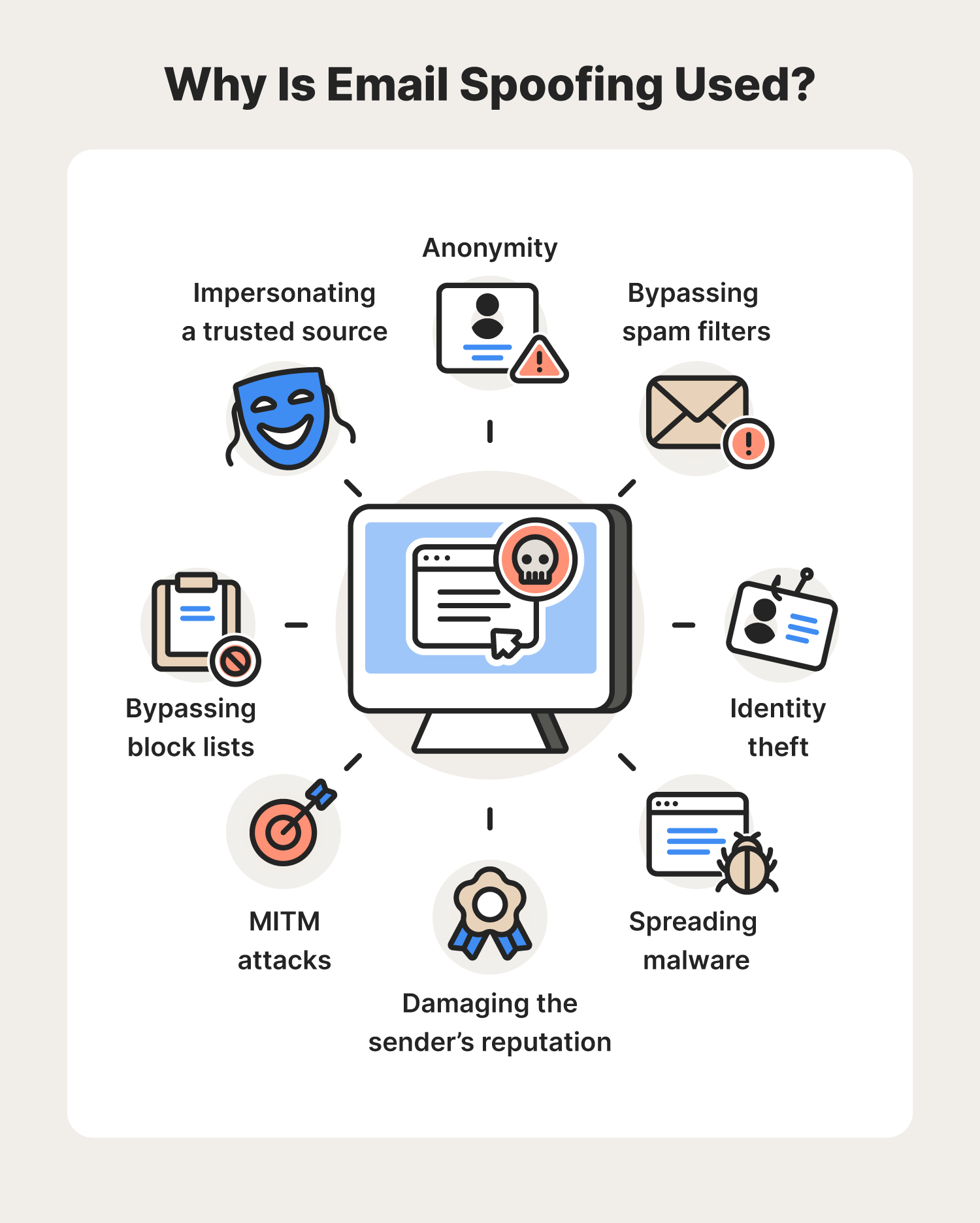
What is email spoofing? A complete guide - Norton

The 10 Worst Cyber Crimes Analysed

Email Security Tech: No Guarantee of Protection from BEC - eftsure
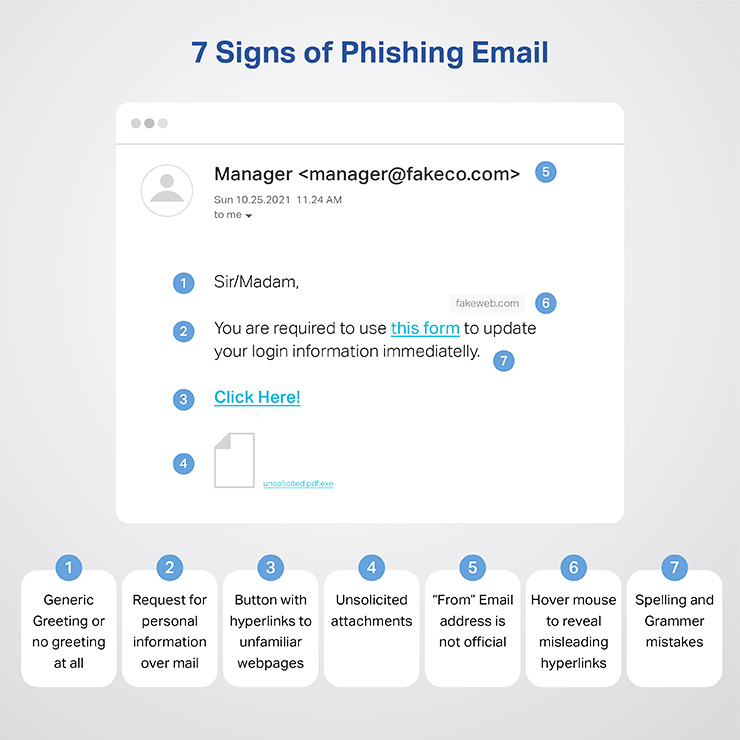
What is Phishing Email: Examples, Types, Techniques & more

4 Key Takeaways From Cofense's Email Security Report 2023 - Talion

Look But Don't Touch: Hackers Sending Targets Image-Based Phishing Scams

FBI: Cybercriminals Are Bypassing Multifactor Authentication

The evolution of ransomware: Lessons for the future

Cybercrime: The Dark Side Of Entrepreneurship

Cybersecurity 101: Everything on how to protect your privacy and stay safe online

Understanding Phishing Emails: Why They Slip Through Spam Filters

Four ways cybercriminals can hack passwords
de
por adulto (o preço varia de acordo com o tamanho do grupo)







